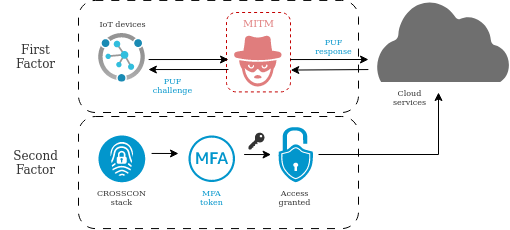
UC1: Device Multi-Factor Authentication
The Internet of Things (IoT) has transformed our way of life and work by connecting everyday objects to the internet and enabling them to communicate with one another. However, this increased connectivity also poses new security challenges, particularly in terms of ensuring that only authorized devices can access the network or other specific resources.
To address this challenge for IoT devices with limited computational resources, Physically Unclonable Functions (PUFs) have been proposed as a lightweight solution for authentication. PUFs are specialized circuits or components that generate unique, unpredictable values based on physical characteristics such as manufacturing variations.
Despite its potential, implementing PUF-based authentication in practice has proven to be challenging and vulnerable to various attacks. To overcome the limitations of existing PUF-based solutions and provide more robust defense against Man-in-the-Middle (MITM) attacks, we propose a multi-factor authentication approach that combines multiple factors.
The ultimate objective of this use case is to propose a multi-factor authentication (MFA) solution for IoT devices that enhances their security, as depicted in Figure 1. Although the original concept was inspired by devices that utilize PUFs and other device-specific factors, our plan is to expand it further to offer a more general MFA solution.
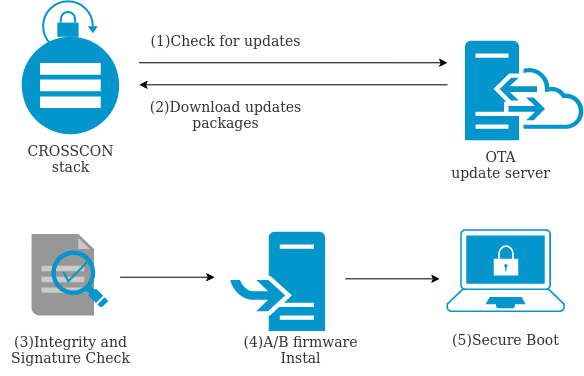
UC2: Firmware Updates of IoT Devices.
Firmware update is a critical process for IoT device security. Not being able to update IoT device firmware is one of the most common sources of vulnerability during the device lifecycle. Furthermore, an insecure update process also presents a major issue as it allows an attacker to upload malicious logic on the device.
Typically, firmware updates are installed Over-The-Air (OTA). Updates and security patches can be digitally signed, such that their integrity and authenticity can be verified. However, despite digital signatures, the problem of secure updates still persists, since: i) updates often come as a bundle of libraries developed by different parties, ii) the signatures are not always issued by a mutually trusted certification authority, iii) digital signatures do not give any guarantee on the logic of the update. This use case, considers two types of updates:
- Full update: the package contains the full replacement of the old package to be installed regardless of what the previous firmware installed was.
- Partial update: the package contains just the binary difference between the new firmware version and the old firmware version. In this case, the device has to reassemble the firmware package using the binary difference (diff) and the old package.
As described in recent studies such as [8] and [9], it is very common to find IoT devices in the field without a secure firmware update system. Even those devices having firmware update mechanisms are in many cases not updated. The main reason is that current solutions cannot provide enough trust to device operators because they can’t manage challenges such as poor network connectivity, management of the device resources to ensure minimal downtime or address a heterogeneous footprint of different hardware and software stacks within the same deployment. In [10] the authors present an analysis performed over a total of 1.061.284 devices in the field and show the average age of the installed firmware is 19.2 months, meaning device firmware is not even updated once a year, leading to many vulnerabilities uncovered during large periods of time.
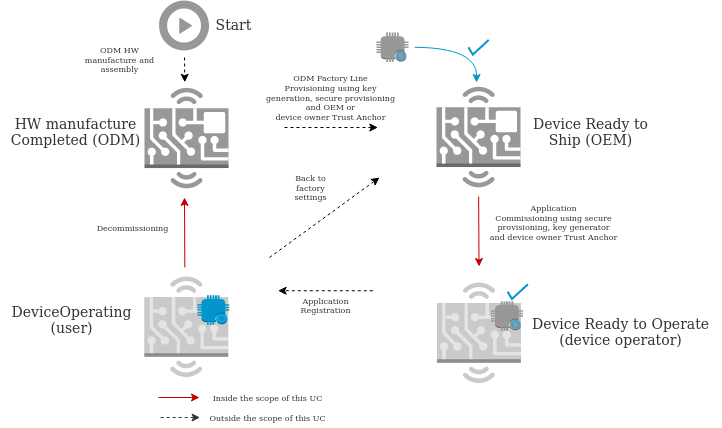
UC3: Commissioning and Decommissioning of IoT devices.
IoT Device Commissioning is the process by which connected devices acquire the necessary information and configuration parameters for their intended use or application: this can include security certificates, credentials, application configuration such as URLs, and others.
Commissioning is a critical step in the IoT device lifecycle, and it needs to happen before the device starts to perform its regular operation.
As opposed, IoT Device Decommissioning is the process by which the commissioned information is removed from the device. This way the device gets back to its original state when it will no longer be used or used for a different purpose or customer. This is important, especially in the case of industrial devices that may contain sensitive information.
Figure shows a typical state diagram of an IoT device lifecycle around the commissioning and decommissioning processes in a multi-stakeholder case, marking in red those processes which are part of the use case addressed by CROSSCON in this project.
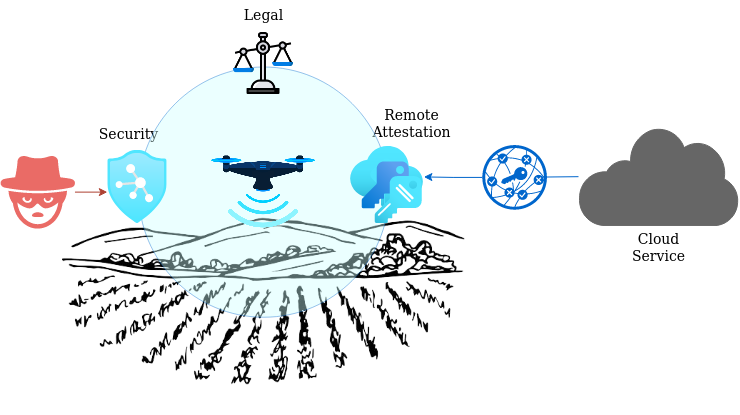
UC4: Remote Attestation for Identification and Integrity Validation of Agricultural UAVs
Agricultural UAVs (Unmanned Aerial Vehicles), also known as agricultural drones, are becoming an increasingly important tool in modern agriculture. These UAVs are equipped with sensors and cameras that can gather data on crops and soil, allowing farmers to make more informed decisions about planting, fertilization, irrigation, and pest control.
Some of the benefits of using agricultural UAVs include:
- Improved efficiency: UAVs can cover large areas of farmland quickly and accurately, reducing the time and cost of traditional methods such as manual labor or satellite imaging.
- Precision agriculture: UAVs can provide detailed, high-resolution data on soil moisture, nutrient levels, and plant health, enabling farmers to apply fertilizers, pesticides, and water precisely where they are needed, reducing waste and increasing yields.
- Reduced environmental impact: By providing farmers with precise data, agricultural UAVs can help reduce the amount of pesticides and fertilizers that are applied to crops, minimizing their impact on the environment.
- Increased safety: UAVs can be used to monitor crops and livestock without putting farmers at risk of injury or exposure to hazardous chemicals.
While agricultural UAVs offer many advantages, they also pose some security-related challenges that need to be addressed such as:
- Privacy concerns: Agricultural UAVs can gather a large amount of data on crops, soil, and other aspects of farmland, raising concerns about privacy and data security.
- Unauthorized access: Agricultural UAVs can be stolen, hacked or used for malicious purposes if they fall into the wrong hands, potentially causing damage to crops, property, or even human life.
- Legal and regulatory compliance: Agricultural UAVs are subject to a range of regulations and restrictions, such as registration requirements, flight restrictions, and privacy laws, which can be complex and difficult to navigate.
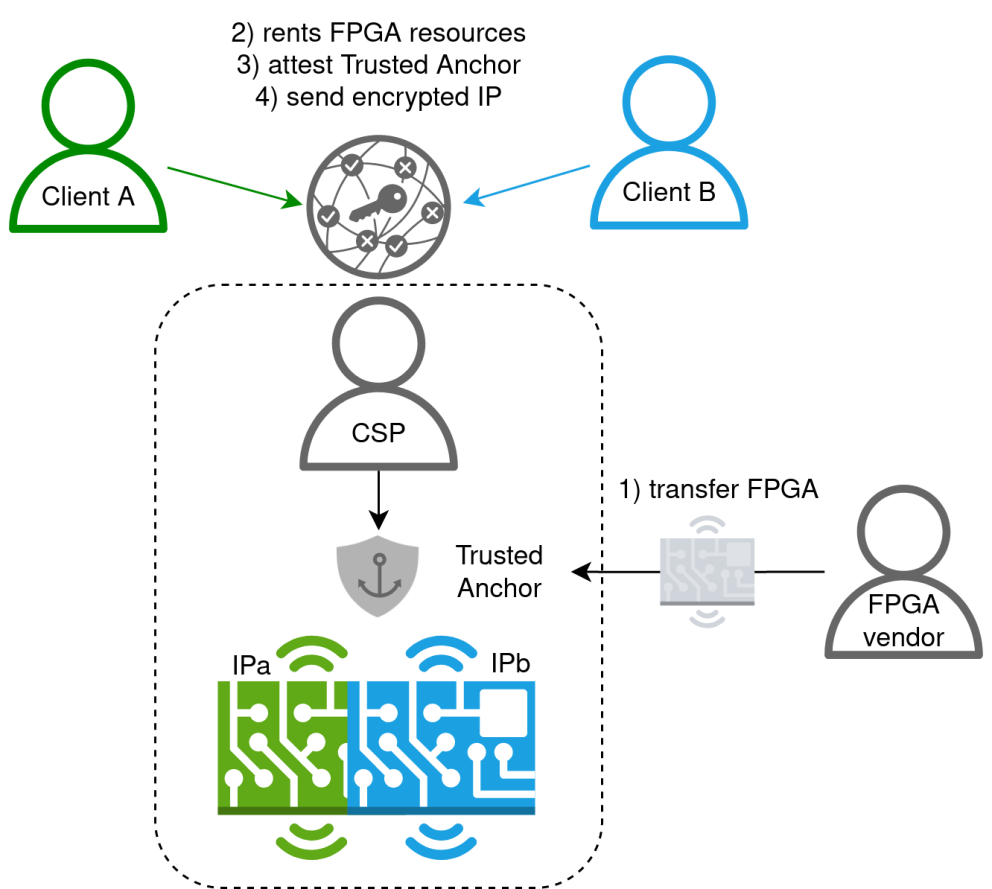
UC5: Intellectual Property Protection for Secure Multi-Tenancy on FPGA
Due to limitations in computational and memory capacity, many IoT nodes are limited in what kind of workloads can be executed on them. Especially compute-intensive tasks related to, e.g., training and inference of AI algorithms can be too heavy operations for IoT devices to handle themselves. There is therefore a need to offload compute-intensive tasks to accelerator nodes that are accessible over the network. In particular, FPGA-based accelerators offered by Cloud Service providers are here of interest, as they offer the possibility for highly efficient computations of compute tasks optimised for the the task at hand.
To reduce the cost of such “FPGA as a service” offerings, it is highly desirable for the cloud service providers to be able to provision the compute workloads of several different clients onto the same FPGA fabric, thereby enabling multi-tenancy on the FPGA. A key question here is, how secure multi-tenancy can be assured so that workloads of one tenant can not have adverse effects on the workloads of other tenants or the FPGA fabric itself and does not lead to unintended leakage of private information processed on the FPGA.
One can distinguish between temporal and spatial multi tenancy. In temporal multi-tenancy, only one client has access to the entire FPGA fabric at a time. Multi-tenancy is thus achieved through alternation of the entire FPGA resource to different clients at different times. The goal of this use case is therefore to demonstrate secure spatial multi-tenancy on an FPGA fabric offered as a cloud-based service. The particular challenge to be solved here is related to the confidentiality of the proprietary IP to be provisioned on the FPGA: How can the cloud service provider verify that the IP does not contain any malicious payloads potentially having adverse effects on the FPGA or leading to data leakage of other tenants, while at the same time preserving the confidentiality of the IP in order to protect the client’s intellectual property?