
Authors:
Carlo Ramponi, Ph.D. Student at University of Trento
Why Memory Safety Still Matters
Despite decades of research, memory safety remains the number one source of critical software vulnerabilities. In 2023, Google reported that nearly 75% of zero-day exploits stemmed from memory safety bugs, while CISA estimated that about 70% of Microsoft’s CVEs were caused by similar issues.
These bugs plague platforms from web browsers to embedded systems, showing that protecting memory access boundaries and lifetimes is still one of the hardest problems in computer security.
Memory Tagging: A Hardware-Supported Path Forward
A promising direction to improve memory safety is memory tagging, a hardware extension that:
- Assigns a tag (or color) to each memory allocation.
- Stores a tag in each pointer.
- Enforces that a memory access is only valid if the pointer tag matches the memory tag.
If the tags mismatch, the hardware blocks the access, effectively detecting spatial memory violations such as buffer overflows.
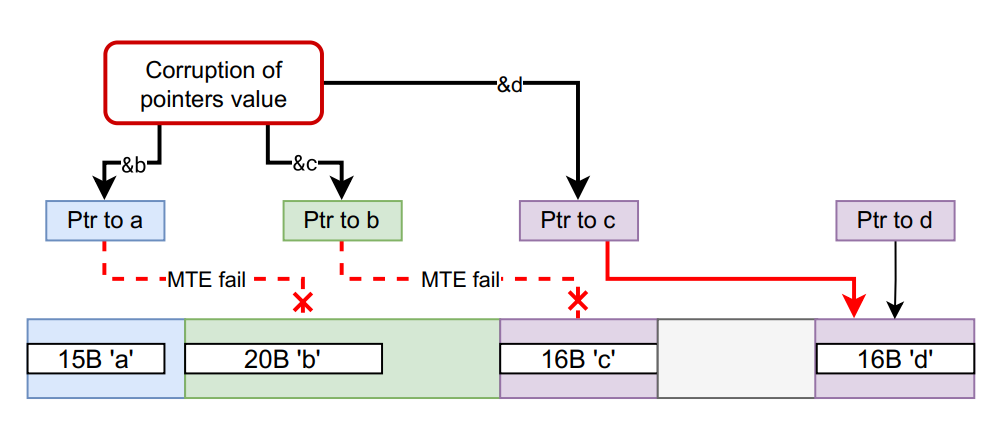
ARM introduced Memory Tagging Extension (MTE) in ARMv8.5-A, and similar proposals are now being explored in the RISC-V ecosystem. In our work, we focus on the TEE TG MTE proposal for RISC-V.
Memory Tagging on RISC-V
Since no hardware support exists yet, we implemented memory tagging on QEMU, extending the RISC-V emulator with new RISC-V instructions for tagging, a dedicated tag memory, new control-status registers (CSRs) and modified load/store operations with tag checking.
While emulation cannot provide accurate performance results, it allows us to explore limitations and solutions ahead of real silicon support.
Tackling the Weakness: Tag Integrity
Memory tagging comes with challenges:
- Limited tag entropy: With 4-bit tags (configurable up to 8 bits on RISC-V), only 16 distinct values exist, leading to tag reuse and collisions.
- Granularity issues: Coarse-grained tagging misses intra-object overflows.
- Tag integrity: Since pointer tags are stored in the pointer itself, attackers can corrupt them to bypass protection.
The last point is particularly concerning: by manipulating pointer arithmetic, an attacker could effectively “recolor” a pointer and gain unauthorized access.
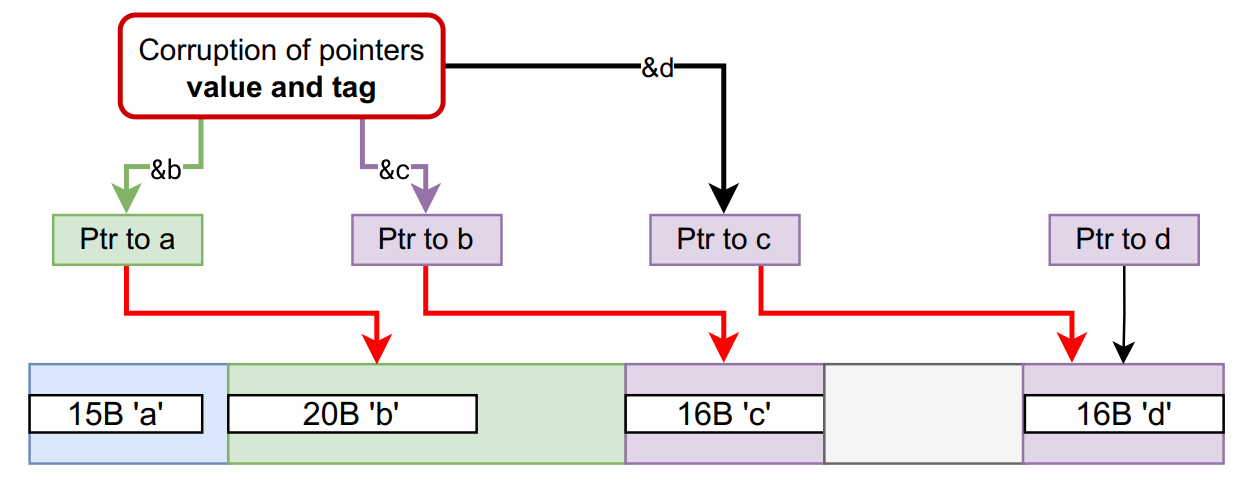
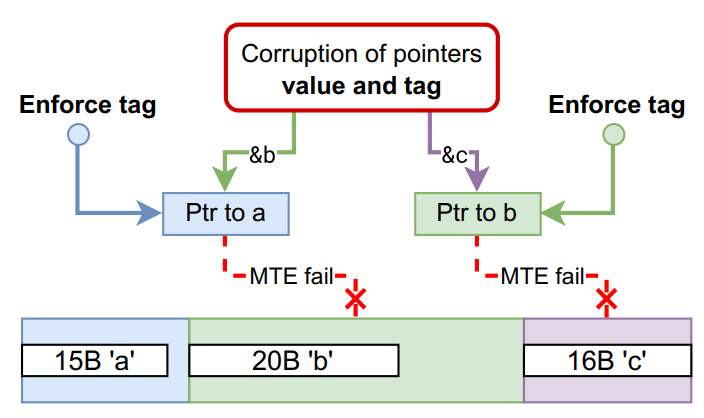
To address this, we developed a software-based integrity mechanism:
- We keep track of the expected tags of live pointers in reserved registers.
- At every dereference, we instrument the code (via LLVM passes) to enforce or restore the correct tag.
- With a static coloring algorithm, we can even optimize and apply persistent tagging efficiently.
Conclusions
Memory safety remains a major root cause of vulnerabilities, with significant real-world impact. Memory tagging provides an efficient hardware-assisted solution, but its limitations, especially tag integrity, must be addressed.
Our LLVM-based approach introduces persistent tagging enforcement, ensuring robust protection even against sophisticated pointer corruption attacks. With these advancements, we aim to bring memory-safe RISC-V systems closer to reality, aligning with CROSSCON’s vision of secure and trustworthy computing for Europe and beyond.