
Author: David Cerdeira, University of Minho
Trusted Execution Environments (TEEs) are secure execution environments that provide hardware-based isolation and protection for Trusted Applications (TAs) and data on a device. They are designed to offer a secure computing environment that is isolated from the main operating system and other applications on the device, i.e., the Rich Execution Environment (REE). TEEs use a combination of hardware and software security mechanisms to ensure that sensitive data and operations are protected from malicious attacks, even if the device is compromised.
With the increasing use of IoT devices in various domains such as healthcare, transportation, and smart homes, the need for robust security measures has become more urgent than ever before. Secure communication, authentication, and privacy protection are some of the key features TEEs provide to the IoT ecosystem. For example, TEEs can be used to protect the confidentiality and integrity of biometric data used for authentication, prevent unauthorized access to medical devices, and secure sensitive financial transactions. TEEs also enable secure firmware updates, which are critical for maintaining the security and functionality of IoT devices.
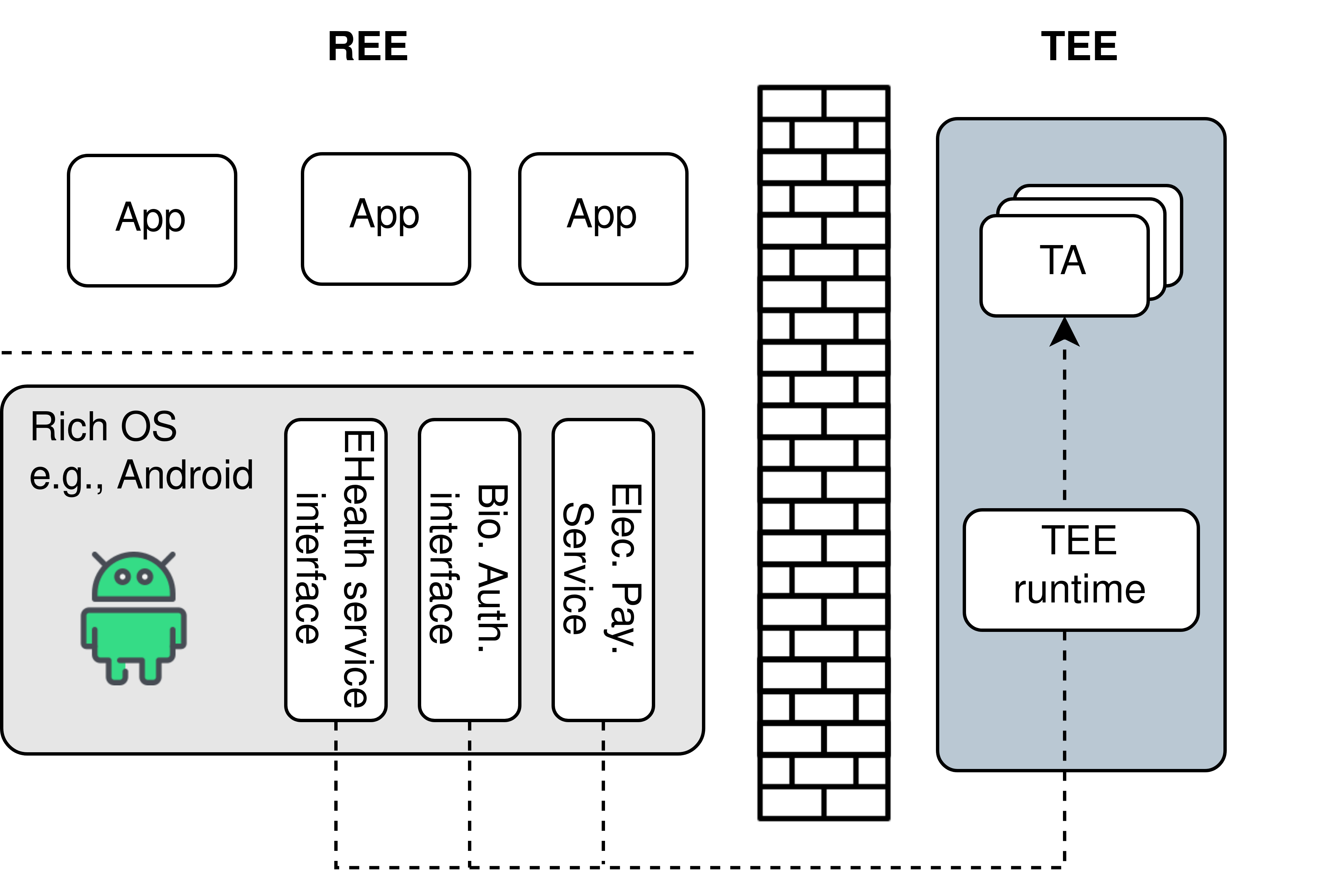
Often implemented through CPU security extensions, such as in Arm TrustZone, TEEs establish at least one protected domain that hosts security-sensitive data and operations. In the case of TrustZone, the security extensions create a secure world (to host the TEE) and a non-secure world (to host the REE) on the same CPU, with each world having its own memory, resources, and security policies. Arm TrustZone is available in both Arm Cortex-M (e.g., Cortex-M 23) and Arm Cortex-A (e.g., Arm Cortex-A53) family of processors.
Although trusted to achieve various security goals, TEEs are not a silver bullet. For example, TEE technology cannot protect against vulnerable TEE code. Poorly programmed TAs may allow attackers to extract secrets, or even enable further exploitation of additional vulnerabilities, which may result in compromising the TEE runtime itself. Due to the nature of these systems, with control over a compromised TEE runtime, attackers may gain full control over the device, completely undermining any established security policies.
As the use of TEEs continues to grow, it is important for researchers and practitioners to be aware of the limitations of these systems and to work towards developing new solutions to address these challenges. This is why in CROSSCON we are looking into using virtualization techniques to address the limitations of current TEEs. With virtualization, multiple isolated execution environments can run on the same hardware, each with its set of resources. These features provide an additional layer of security for sensitive applications and data, making it more difficult for attackers to compromise security-sensitive data and operations.
Despite the limitations, TEEs are an essential component of modern IoT systems and play a critical role in providing security to sensitive workloads. Their importance will only continue to grow as more devices become connected and the need for secure computing environments becomes more pressing. In the context of the CROSSCON Project, we are working on the CROSSCON-TEE, an enhanced solution that overcomes current TEEs limitations by adopting virtualization techniques.
Stay tuned for further developments!