Author: Malvina Catalano Gonzaga, CYSEC
Introduction
The Internet of Things (IoT) has revolutionized the way we interact with technology, embedding connectivity into everyday objects and systems, driving a rapid expansion of connected devices across many sectors. However, with this growth comes significant security challenges, and ensuring their security is fundamental. Vulnerabilities in IoT systems can lead to severe consequences, including data breaches, unauthorized access, and even control of essential services. Thus, embedding robust security measures into IoT devices is crucial to protect not only individual users but also broader societal functions, making security a foundational aspect of IoT development.
IoT security encompasses a broad range of practices and technologies designed to safeguard devices, networks, and data from unauthorized access, attacks, and breaches. This includes securing communication channels, ensuring data integrity, and implementing robust authentication and access controls.
Challenges of Embedding Security in IoT Devices
Implementing security measures in IoT devices presents many challenges due to the diverse and often constrained nature of the hardware, the massive scale of deployment, and the lack of standardized protocols.
Following are the four biggest hurdles to ensure the security of IoT devices:
- Diverse Hardware Platforms: IoT devices range from low-power sensors and simple actuators to high-performance gateways and complex edge devices, each with distinct computational capabilities and resource constraints. This variety makes it difficult to implement uniform security measures, as solutions suitable for powerful gateways may be impractical for resource-constrained sensors. Furthermore, the lack of standardization across different manufacturers and platforms aggravates incompatibility issues, leading to fragmented security implementations.
- Resource Constraints: many IoT devices, especially low-power sensors and actuators, have limited processing power, memory, and energy resources. These limitations make it challenging to implement robust security features that are typically resource intensive. Security measures such as encryption, secure boot processes, and real-time monitoring require substantial computational and memory resources, which can strain the limited capabilities of these devices.
- Scalability: managing security for millions of devices presents substantial challenges, including maintaining an up-to-date inventory of devices, monitoring for vulnerabilities, and deploying security patches promptly. Ensuring consistent security updates is particularly hard, as IoT devices often have varying capabilities and may be dispersed across remote or hard-to-reach locations. Automated update mechanisms and centralized management platforms are essential to streamline this process, but they must be designed to handle the scale and diversity of the IoT ecosystem.
- Interoperability: interoperability poses a significant challenge in IoT security due to the wide range of proprietary technologies and protocols employed by different manufacturers. This diversity leads to a fragmented ecosystem where devices from different vendors may not easily communicate or work together, complicating the implementation of a unified security framework. The lack of standardization means that security solutions must often be tailored to specific devices or networks, increasing complexity and cost.
CROSSCON’s Contribution to IoT Security
CROSSCON addresses those challenges by developing an open and vendor-independent security stack. The goal of the project is to create a consistent security baseline across diverse IoT systems, which include:
- A wide range of devices with varying hardware capabilities
- A unified set of APIs that facilitate interoperability across different devices and platforms, allowing for security features to be configured according to individual requirements and the specific underlying hardware of each device.
- A Trusted Execution Environment (TEE) implementation when no existing security features are available, ensuring robust security even in resource-constrained environments.
- Secure delivery mechanisms and security protocols, like remote attestation, to maintain and verify the integrity and authenticity of software and firmware updates.
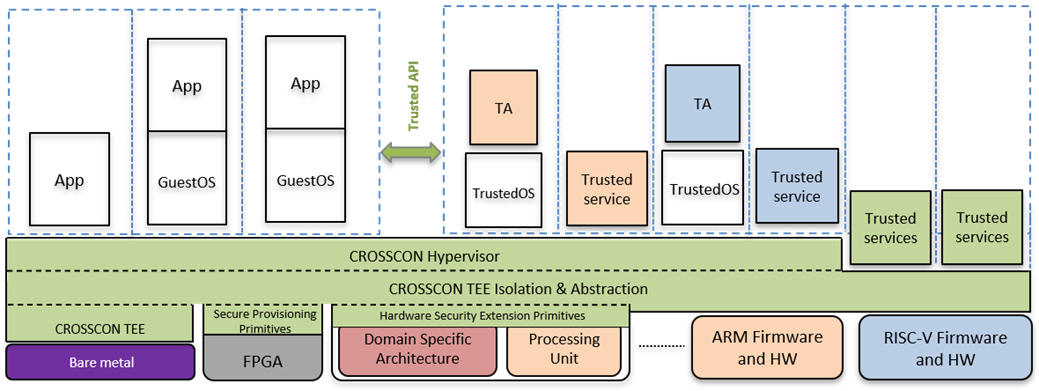
The image below provides an overview of the CROSSCON’s architecture, showing how it integrates various hardware platforms and security mechanisms, while also highlighting how CROSSCON establishes a unified framework, ensuring robust protection and interoperability across different IoT devices and environments.
Conclusion
Embedding robust security in IoT devices is essential yet challenging due to diverse hardware platforms, resource constraints, scalability issues, and interoperability problems. These challenges necessitate innovative and adaptable security solutions to protect the vast and varied landscape of connected devices. The CROSSCON project is a significant step forward in addressing these issues by providing an open, vendor-independent security stack that ensures a consistent security baseline across IoT systems.